Government hackers were behind most of the zero-day exploits linked to real-world cyberattacks last year, according to a new report from Google.
The report reveals that 75 zero-day exploits were used in 2024, down from 98 the year before. But of the cases Google could trace to specific actors, government hackers were the main culprits. At least 23 of these exploits came from state-backed groups.
Among them, 10 were tied directly to government hackers, with five linked to China and five to North Korea. Google also flagged eight exploits created by spyware vendors. These vendors often claim to work only with governments, yet their tools have ended up in controversial hands. For instance, some of these exploits were used by Serbian authorities through Cellebrite’s phone-unlocking technology.
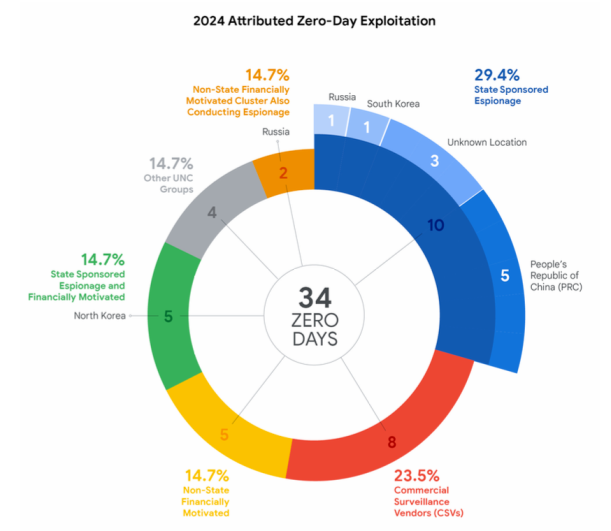
Another graphic in the report shows 34 exploits traced back to specific sources. Ten were tied to espionage by government hackers, and eight came from commercial surveillance vendors.
Even as spyware firms grow more secretive, they are putting more effort into hiding their methods. Google notes that despite enforcement efforts pushing some companies out, new vendors are stepping in to fill the gap. As long as governments keep buying these tools, the market will continue expanding.
The report also identifies 11 zero-days likely used by criminal groups. These included ransomware gangs targeting enterprise devices like VPNs and routers.
Most of the 75 zero-day exploits focused on everyday tech, like phones and web browsers. The rest targeted tools used inside company networks.
But there’s some progress. Google says that software makers are making it harder for attackers to find flaws. In fact, there’s a noticeable drop in exploits against browsers and mobile operating systems — once favorite targets.
Some defenses are working especially well. Lockdown Mode, a feature on iOS and macOS, helps block attacks from government hackers. Google also points to Memory Tagging Extension (MTE), found in its Pixel chipsets, which helps detect bugs before they cause harm.
While many zero-day attacks remain hidden or unattributed, reports like this shed light on the tactics and trends used by government hackers and others. Knowing who is behind the attacks helps the cybersecurity industry respond faster — and smarter.













